Analyzing the Past
One of the most challenging (and frustrating) components in the never-ending cycle of white hats chasing black hats is the length of time it takes to build methods of detecting new attack vectors. The creation of signatures and Indicators of Compromise (IOCs) requires long periods of monitoring, response and research. This creates (potentially long) windows of time when attackers can lurk in networks. Once IOCs can be crafted surrounding a specific threat, they need to be retroactively applied to the data collected during the “dark period.”
Pervasive Logging
The foundational element in retroactive network forensic analysis is proper log collection and archival. The Lancope StealthWatch System is architected to archive months or years of communication records going in, out and around a global enterprise network. The records are collected from NetFlow-enabled routers, switches and firewalls. Additional deep packet visibility is provided by strategic placement of StealthWatch FlowSensors in the network. These records are all forwarded to a StealthWatch FlowCollector, which combines the collective data from every network device into an intelligent, cohesive record of every communication.
Asking Any Question
When data becomes available through either global intelligence like the Mandiant APT1 Report or internally as incident responders are able to build threat profiles, those markers can be fed into the StealthWatch System to return a precise data set of suspicious communications.
Date/Time
If the attack time is known, it can be defined specifically, or the query can be applied to all archived flows.
Hosts
The server or client IP addresses, ranges or host groups can be specified.
Interfaces
The networking interfaces that the traffic routed across can be specified to determine how prohibited behavior was able to circumvent enforcement mechanisms.
Services, Applications, Ports and Protocols
The ports and protocols can be filtered. If StealthWatch FlowSensor or Cisco NBAR visibility is enabled, traffic can be filtered on deep packet inspection recognition of networking applications.
Routing
Traffic can be filtered by DSCP, AS Numbers, VLAN ID and MPLS labels to further tune the result set.
Traffic
Total bytes exchanged, bytes consumed by the client or sent to the server can also be queried in ranges.

Performance
Where FlowSensor enhanced flows exist, the number of TCP connections, retransmissions, round trip times and server response times can be used as an advanced marker.
Application Details
When traffic crosses a FlowSensor, the first 1 to 256 bytes can be collected and archived with the flow record. This allows queries to include matches on SSL certificate names, URL or FQDN.
Advanced
Leveraging Cisco NetFlow Secure Event Logging (NSEL) from ASA Firewalls, flows can be limited to the action the firewall took on the communication (permit/deny).
Example IOC Usage
Following are common IOC queries.
Blacklisted IP Addresses
In the screenshot below, the IP addresses listed in the StealthWatch Labs blog post, New APT1/Comment Crew Indicators, are entered into a flow query to retroactively look for any communications to these IP addresses associated with APT1/Comment Crew.

Known Bad Ports
When non-conventional ports are noted in IOCs, they can also be queried. In the example below, abnormal ports from the FireEye “H-worm by Houdini” blog post are searched historically.

Searching for FQDN
In StealthWatch System environments that have application awareness from FlowSensors, the URL requested in HTTP traffic can be appended to the FlowObject. Since DNS records can be updated at different parts of an attack cycle, it is helpful to have stored domain names and URLs in flow records. The example below shows the query to look for the FQDN IOC produced by StealthWatch Labs.

If the query should be limited to URL requests via HTTP, the application should be restricted to HTTP as shown below.

Searching for SSL Common Names
Another common IOC is searching for common names in SSL certificates. In the same manner that FlowSensors collect URL information on HTTP traffic, they can also collect common names (CN) from SSL certificate exchange. The Mandiant APT1 Report included several CNs useful in retroactive analysis. Below is a screenshot.

Using the Results
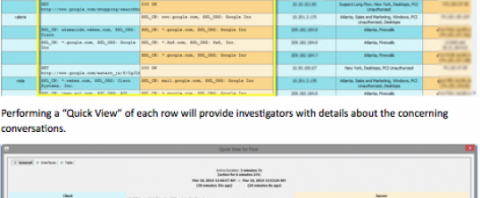
In the example below, a simple query is made looking for all requests that used “google.com” in the request.

The results are displayed in a tabular view that can be exported to CSV or examined more fully in the StealthWatch System.

Wrap Up
As Indicators of Compromise become available, it is critical that organizations apply them to historical data to determine if a breach has occurred. The StealthWatch System provides a processing and storage engine that allows organizations to accomplish this task.
More information on this concept can be found in the recent Gartner report, “Malware Is Already Inside Your Organization; Deal With It.”1 According to the report, “Security organizations must assume they are compromised, and, therefore, invest in detective capabilities that provide continuous monitoring for patterns and behaviors indicative of malicious intent.” The report discusses network analysis by Lancope as a technique for detecting IOCs.
1 – Gartner, Inc., “Malware Is Already Inside Your Organization; Deal With It,” February 12, 2014, Peter Firstbrook & Neil MacDonald, #G00259857
