What is SQL Injection?
South Carolina recently made the news as more than 3.6 million social security numbers were stolen from a public facing website. While it hasn’t been verified by SC officials, most information security experts believe the most likely method of data exfiltration in this case was an SQL injection.
SQL injection is a favored attack vector for hackers wanting to steal protected information. Over the last year we have seen repeated reports of disclosed information ranging from email addresses to credit card numbers all delivered via this type of exploit. SQL injection attacks can be launched against web servers that use a backend database to generate web pages. These web servers normally only use specific portions of the information in the database and access to the data is controlled by the web application’s coding. An SQL injection attack allows the attacker to bypass that coding and communicate directly with the backend database server using the web server as a conduit.
Intelligent processing of NetFlow data can both detect and prevent data loss that occurs by SQL injection. Let’s take a look at how Lancope’s StealthWatch System and NetFlow can provide actionable intelligence into every stage of an SQL injection attack.
Phase 1: Discovery and Fingerprinting
Before an attack can occur an attacker must first answer a series of questions:
- How many web servers are there?
- What TCP ports are web services running on?
- Which web servers have access to the backend database?
- What web server is running (IIS, Apache, etc.)?
- What programming technology is running on the server (PHP, ASP.NET, Ruby, etc.)?
- Is the application out-of-the-box, open source or custom?
Discovery
The attacker needs to answer these questions to determine what type of SQL injection may work. To accomplish this, the attacker will begin scanning the subnet the web servers are in to answer the first question. This portion of the attack will generate what StealthWatch calls Concern Index (CI) events. CI events are actions a host performs that are reason for concern. Some actions are more concerning than others and subsequently will accumulate points commensurate with the degree of concern. In the case of our attacker, 1.7M points of CI were logged as he was attempting to answer the first two questions.

That accumulation of CI resulted in a “High Concern Index” alarm against his machine less than two minutes into the attack. If set up to do so, this alarm could have also triggered an automatic mitigation response in StealthWatch (i.e. sending a SHUN command to the firewall) that would have prevented the attacker from getting any further.

Fingerprinting
Once the attacker had discovered the web server to exploit, the process of fingerprinting the web service to find exploitable vulnerabilities began. The attacker tried multiple Layer 4 types of scans to better understand the service to be exploited. This further increased the Concern Index.

Since the attacking host had already developed a bad reputation (high CI), once it established a communication with the web server, an alarm was raised on the web server called a Touched Host alarm. A Touched Host alarm occurs when a suspicious host begins to have bi-directional conversations with a network resource. This is another condition that would notify operators and could trigger mitigation.

The number of connections that are necessary for this type of fingerprinting generates alarms as well.

Exploit Attempts
Once the service has been profiled, the attacker attempts thousands of different requests designed to determine what exploit will gain access to the database via SQL injection. This can be observed by the number of TCP connections the attacking host has with the target.

Phase 2: Steal the Data
Once the attacker is able to craft an effective exploit, the information will leave the database, flow through the web server and be delivered to the attacker. Graphing the traffic between the web clients and web server as well as the web server and database server shows the exfiltration clearly.


Zooming in on those spikes and looking at the flows causing them, we can determine that the attacker downloaded 6.38GB of information from the web server and the web server received 4.83GB of information from the database.

These communications each would trigger anomaly alarms because of their deviation from normal, baselined traffic profiles. This is another step where the download could be disrupted through mitigation or response.


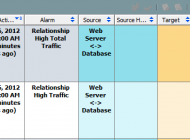
In addition to these alarms on the servers, the attacking host will also flag an alarm for high total traffic.

These types of alarms against outside hosts that are consuming abnormal amounts of data from the network are clear indicators of data exfiltration. They deliver actionable intelligence for internal investigations and to provide to law enforcement.
Determining Impact
Utilizing data provided by the StealthWatch FlowSensor Virtual Edition (VE) installed on the VMWare ESX server hosting the web server and on the database server, we are able to pull deep packet inspection details that show us that the page that was exploited on the web server was called “comment.php.”

Intelligent NetFlow analysis can provide deep visibility into an SQL injection at several stages of the assault. The mitigation can be automatic or authorized by an operator. Mitigation can range from blocking the traffic at a firewall to advanced actions including routing traffic into a Honeynet. NetFlow analysis provides the actionable intelligence needed to prevent, mitigate and respond to data exfiltration of this type. For more information on detecting data loss with StealthWatch, to go: http://www.lancope.com/solutions/security-operations/data-loss/.
