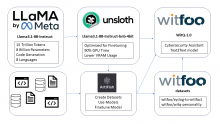
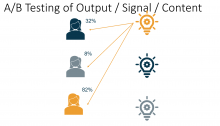
People > Machines (The OODA Loop Strikes Back)
Why I'm Not Losing Sleep Over AI Stealing My Job or My Soul
Teaching Claude the Old Tricks: Lessons from Migrating Legacy Code to an AI-Assisted Workflow
Coding with Claude: What I've Learned Building a Cybersecurity Platform with AI
Cricket Baptism
Empathetic Processing and Temporal Link Analysis: Research Pathways for AI in Cyber Defense
New Zealand Move Notes
Background
Over the course of a year from November 2025 to November 2026, Mai and I researched and eventually moved to New Zealand. We were looking for a life change and my work at WitFoo needed to plan for international expansion. My extensive notes are found below.
Advisors
Our move was made much easier by a few advisors. I am pretty good at paperwork and research and thought of doing it myself to save some money. I ended up feeling that all 3 of these advisors over delivered on value and made our move much more successful.
Tags
The Wizard, The Warrior and The Poet
In the labyrinth of our professional lives, the roles we assume can often feel overwhelming. Balancing strategy, execution, and inspiration requires a delicate dance of various skills and mindsets. To navigate this complexity, I have compartmentalized my work into three distinct personas: The Wizard, The Warrior, and The Poet. Each persona plays a vital role in the tapestry of my professional endeavors, allowing me to approach challenges with clarity, purpose, and creativity.
The Wizard: Master of Strategy and Vision
The journey begins with The Wizard, a figure of wisdom and foresight. When I don the robe of The Wizard, I immerse myself in the realm of strategy and planning. The Wizard's primary concern is to devise the best possible strategy, envisioning the grand scheme in its entirety. This persona thrives on considering every facet of a plan, ensuring that all systems and stakeholders are accounted for.
GrrCON 2024 - Birthing Perjury-free AI
Abstract
Cybersecurity analysis leading to deterrence of cybercrime requires processing thousands to billions of digital signals per second. Those signals must be accurately comprehended, forensically preserved then used to detect and investigate potential cybercrime. The work products must not only assist the investigators but must be translated into language that non-technical lay audiences including judges, lawyers and jurors can understand.
This presentation explores how generative artificial intelligence (GenAI), natural language processing (NLP), graph-theory and artificial narrow intelligence (ANI) can play a role in delivering these outcomes.
The session includes demonstrations of opensource toolkits, datasets and models designed to assist in this work.
TechnoWest 2024 - Birthing Perjury-free AI
ISSA Grand Rapids Talk - Birthing Perjury-free AI
AI Development on Windows 11: Compiling PyTorch
4k UHD Bitrate Deep Dive
ChiBrrCon Talk 2: Birthing Perjury-free AI
Abstract
While believability of an AI (Turing test) is important in many applications, the need for forensic truth is paramount in cybersecurity application. In this session, we will evaluate methods for training and tuning models that meet requirements of evidence handling, business analysis and legal and martial response.
ChiBrrCon Talk 1: SECOPS Driving Criminal Prosecution
AI.Dev and Cassandra Summit 2023 - Building a CyberGrid on Cassandra
On December 12, 2023 in San Jose at the Linux Foundations, AI.dev & Cassandra Summit, I delivered this presentation. The deck and recording is included below.
Mai's Whole Grain Sticky Rice
Vegan Double-Chocolate, Double-Nut Cookies
Fish's Vegan High-Protein Cornbread
Fish's 50 Plant Stew Recipe
DarkRhiino Podcast - 7 Unstable Conversations
7 Rules of "eFishiency"
Machine Learning Driven Social Engineering
GrrCON 2023 - Deterring Cybercrime via a Global CyberGrid
Abstract
Detecting, catching and successfully prosecuting cybercrime requires collaboration across private sector, law enforcement, insurance companies and national security agencies. In this session, approaches to collect, analyze, store and share digital evidence will be examined. Methods of safely transmitting data between private sector and law enforcement will be discussed. Demonstration of workflows between investigators, law enforcement, prosecutors and insurance adjusters will be covered.
I also reference this 2021 DarkReading Article: Handcuffs over AI.