In a recent blog entry, Brian Krebs revealed that a Russian-based service is selling the IP addresses, usernames and passwords of computers inside organizations including Fortune 500 companies using the Remote Desktop Protocol (RDP).
In the blog entry’s comments section, some readers asked how they can check if their servers are listed in the service’s database. While there certainly is merit in that type of diligence, they could better answer that question by reviewing their own network surveillance data, as this specific Russian group is not the only one out there trying to break into systems via RDP.
Lancope’s research team, StealthLabs, has a tool called a Darknet that we use to monitor the Internet for malicious activity. RDP is one of the most common services that people scan for on the Internet, according to the data collected by Darknet. When these scanners find open RDP servers, they brute-force crack usernames and passwords. Over the past 12 months, a self-propagating worm called Morto has also been spreading by brute-force cracking of RDP usernames and passwords. In addition, we see similar scanning, brute-force cracking, and automatically propagating malware targeting other remotely accessible authentication services like Secure Shell (SSH). For these reasons, it is vitally important that remote services like these be limited and monitored.
Enterprise NetFlow/IPFIX can quickly assess whether RPD conversations have been happening between your network and the Internet. With Lancope’s StealthWatch System, affected machines can be found quickly by running a “Top Conversations” report in which enterprise hosts (Inside Hosts) are the servers and everyone else (Outside Hosts) are the clients:

Users can also add a filter for remote desktop services:

That returns a report of all communications that have been made to exposed RDP servers:

* Note that not only are the exposed hosts listed (in Host column) and the exploiting host (Peer column) but also the bytes transferred. This is helpful in determining if the connection was attempted or successful. (Successful connections on RDP will generate much more traffic than an attempted connection that fails due to credentials.)
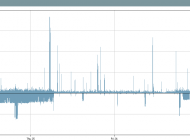
If a user wants to establish trending of this type of traffic, a “Flow Traffic” report with the same filters could also be run to produce the following histogram:

These reports can go months (or years) into the past to determine when the suspect traffic first began.
In StealthWatch, if an identity services solution is in place (such as StealthWatch IDentity or Cisco ISE), users can also determine which credentials on the RDP machines have been compromised.
On top of determining retroactive impact of a compromise, intelligent NetFlow analysis can also alert against future infractions via Host Locking policies:

These policy violations can trigger immediate notifications or be wrapped into regular reports. Host locking provides a means of validating enforcement mechanisms like firewalls and detecting holes in security architecture.
It is a sad state of affairs when we have to buy services from hackers to determine if they have exploited our systems. However, this can be avoided by instead employing proper network surveillance, which can take the guesswork out of determining the relevance of emerging threats. Intelligent analysis of NetFlow/IPFIX data can give timely answers to questions like those raised by Brian Krebs.
For more information on StealthWatch for security monitoring, go to: http://www.lancope.com/solutions/security-operations/.
