Monitoring Protected Data with NetFlow
Introduction
The South Carolina Department of Revenue breach that disclosed 70 gigabytes of taxpayer data to a Russian-based hacker is a great example of how NetFlow could have saved the day. In that particular breach, spear-phished credentials were used to access a VDI machine that pivoted to an internal computer, which transferred the large data dump from a database server.
The pivot machine then moved the 70 GB to another computer before moving it one more time to a destination in Eastern Europe. In a previous blog entry, I described how data loss solutions could have caught this attack by monitoring northbound (egress) traffic. The pervasive monitoring of NetFlow can protect networks much earlier by examining the east-west (lateral) movement of the data. In this installment, we’ll take a deep-dive look at how pervasive, NetFlow-enabled behavioral analysis can catch data loss much earlier in an attack.
Signature-Based Detection Doesn’t Cut It
In another recent blog series, I noted the differences between signature-based detection and behavioral detection. With the exception of “host locking,” which will be discussed later, all of the detection methods covered in this post are behavioral-based. Behavioral detection differs from signature detection in a number of ways, but most notably, behavioral detection requires maintaining and incrementing records on hosts to catalog behavior.
Where behavioral detection is “host-centric,” signature detection is “transaction-centric.” Signature-based detection looks at a data stream, and based on the data of that stream, determines whether that transaction should be red flagged. Behavioral detection takes a broader view, looking at every transaction in context to a host’s criticality, function, location and a number of other metrics.
Setting Up Monitoring
With Lancope’s StealthWatch System, a grouping of computers housing protected data can be created. In this example, we are going to look at how cardholder data can be monitored to ensure PCI compliance. This same approach can be used to monitor access to protected trade secrets, patient data, PII, FOUO (for official use only) or any other data that needs to be safeguarded.
Create the Host Groups
To begin protecting the cardholder data, security administrators need to first establish where it is. I’ve met with several security groups that didn’t know where their sensitive information was located. This is akin to the guards at Fort Knox not knowing where the gold is kept. A fundamental step in safeguarding data is taking an inventory of where it is located. It is likely that the initial inventory will reveal a need to improve segmentation and safeguarding (enforcement) design. Once the data is properly inventoried and segmented, one can add the IP addresses of the protected machines to their own host group.
Create the Relationship
When implementing a segmentation strategy, data relationships and policies should have been created for who/what can access the data. In StealthWatch, users can create host groups for those policy participants – point-of-sale (POS) machines, e-Commerce, accounting, unauthorized segments, etc. With the host groups created, a relational map can be formed in StealthWatch.

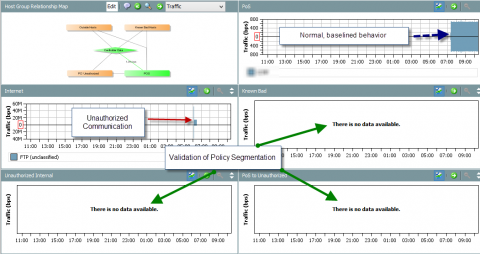
In the example map above, note that only POS machines should have access to the cardholder data. Since a “hole” in security must be created to allow for business operations, these communications need to be closely scrutinized. StealthWatch can baseline what normal traffic profiles look like for this relationship, and send alarms to operators when anomalous traffic occurs.

In our example infrastructure, no traffic should exist on any other links, including those leaving POS machines to unauthorized machines or the Internet.
Examining Compliance Traffic
Histograms of traffic can be created going back as long as the relationships exist to provide auditors with proof that no authorized communications have occurred. In the PCI Operational Dashboard below, note that the authorized communications between the POS machines and the cardholder data stores are being monitored for suspicious and anomalous traffic. Also note that the pervasive nature of NetFlow monitoring easily shows that compliance measures are effective on three of the prohibited relationships. Also note that a policy violation is logged for traffic leaving a cardholder data store to the Internet.

Alarms on Policy Violations
As discussed in another previous blog post, host locking policies can be created to send alarms when segmentation rules are broken.

These hard policy alarms can provide alerts when users have circumvented enforcement mechanisms or policy to reach protected assets. If alerts are desired on attempted (unidirectional) connections, StealthWatch can alert on those attempted breaches as well. This allows detection early in the kill chain.
Marking Assets as “High Sensitivity”
In StealthWatch, every host is assigned a flexible indicator called the Target Index (TI). The Target Index is a numeric value that represents how much suspicious or anomalous activity is being directed at the host. TI is algorithmically calculated and incremented as every communication is processed by the StealthWatch FlowCollector.
When protecting assets containing sensitive information, a “High Target Index” alarm can be initiated to alert operators to active threats against those hosts. TI can be driven up on a host as early as the reconnaissance phase in the kill chain. Since TI is attached to the target (and not the attacking host), sophisticated attacks that are being coordinated from multiple sources (attackers) to reduce suspicion will still be quickly seen because of the target-focused nature of this score. The “tolerance” of bad behavior can be made very low on these protected hosts because of their predictable transaction patterns (mostly POS) and the high sensitivity of the data concerned.

Data Loss
In addition to the early lateral detection provided by intelligent behavioral NetFlow analysis, standard egress monitoring can also be leveraged to note possible data loss.

Forensic Logging
When a breach is detected by human intelligence, behavioral analysis, or another detection mechanism, StealthWatch provides pervasive, forensic records that allow the impact of a breach to be determined.

Wrap Up
Intelligent processing of NetFlow records in conjunction with a behavioral analysis engine can provide early detection of attempted breaches of protected information. Additionally, the deep visibility provides a long-term audit trail that can demonstrate compliance, validate segmentation and enforcement, as well as create long-term forensic records.
Click here for more information on how StealthWatch helps detect and prevent data loss. For further details on NetFlow for compliance, go to: http://www.lancope.com/solutions/compliance/.
