Part 1: History of NBAD
Part 2: NBAD Signature Detection
Part 3: NBAD Behavioral Detection
Anomaly detection in NBAD is similar to behavioral detection in that it relies on counters on the monitored hosts. It differs from behavioral detection in that it monitors against established baseline/trend data and not programmatic algorithms. Another way of saying this is that behavioral detection looks for known bad traffic and anomaly detection looks for any traffic that is not known good. To accomplish this, anomaly detection requires the creation and maintenance of baselines in addition to the host profiles and counters created in behavioral detection.
Data Exfiltration Monitoring
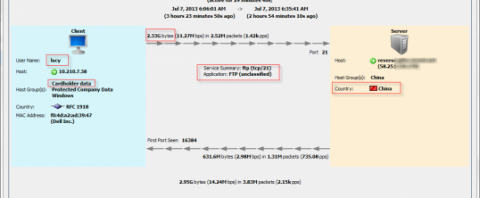
One of the most effective means of host anomaly detection is monitoring for data exfiltration. When it can be determined how much data a host of a certain type (desktop, administrator, server, etc.) is expected to send out of the network a baseline can be established. Each host object of that type can then be assigned a counter that increments when the host sends data out of the network. When the amount established in the baseline (threshold) is exceeded by the counter an alarm for “Suspect Data Loss” can be generated. Note the loss of data outlined below.

Data Hoarding Monitoring
In the same fashion that baselines can be established for sending data from the host to the Internet, baselines and counters can be created to look for abnormal downloads from internal data stores to an internal host. This “Data Hoarding” alarm is particularly effective in NBAD because of the deep network visibility provided by NetFlow. Note: the host below that stockpiled abnormal amounts of data from around the network.
Connection Saturation Monitoring
Baselines can also be established for the number of connections a host creates to other hosts. If a host type is expected to have less than 30 open connections and is observed having several thousand connections open instead, there is valid reason for concern.
Wrap Up
By creating thresholds for acceptable behavior on different types of hosts across the network, NBAD can alert security analysts to advanced attacks or insiders threats. For more details on using NBAD to monitor for advanced insider threats see: Dealing with Insider Threats


