While signature based detection is not the core role of NBAD solutions, the deep visibility NBAD enjoys through NetFlow collection allows for effective detection of several types of “known bad” connection scenarios.
Watch Host/Watch Port
Since NetFlow and other NBAD data sources contain layer 3 (IP address) and layer 4 (port) data, alerts can be created when hosts (IP) or port traffic is observed on the network.

The benefit of doing this monitoring in NBAD as opposed to traditional signature detection tools is the deep visibility provided to NBAD. Access or core switches can see these violations much sooner than probe based products. When purposeful monitoring is started on one or more internal hosts, Watch Host alarms can trigger investigative processes with responders or other tools.
When alarms need to be generated on port use, Watch Port active can also be utilized to alert analysts and responders.

Host Lock Violation
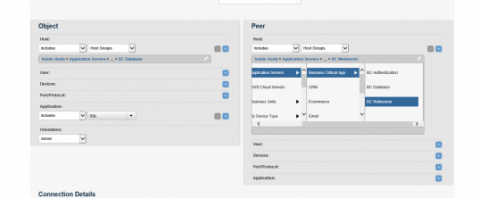
An evolution of Watch Host and Watch Port is Host Locking. Host Locking allows a combination of client and server IP addresses as well as services or ports being utilized. This approach is effective in segmentation validation (see: Monitoring Protected Data with NetFlow) and policy enforcement (see: When Enforcement Doesn’t…). Below is an example of a Host Locking Rule ensuring that connections to a Citrix VDI from East Asia are being blocked.
Botnet Detection
With the use of enhanced probes (i.e. StealthWatch FlowSensor) that can collect application details and the incorporation of threat details (i.e. SLIC Threat Feed) alarms to known BotNet Command and Control (C&C) servers can be generated. Note the alarm below on a host connecting to a C&C Server from the Blackenergy Botnet family:
Custom Criteria
In StealthWatch 6.5, User-defined Threat Criteria allows custom signatures to be created using a wide range of data collected for NBAD processing. See the example below that outlines a signature designed to detect SQL Injection occurring on a business critical web application.
Wrap Up
While NBAD is most noted for its behavioral and anomaly detection capabilities, it’s pervasive visibility into the network via NetFlow processing allows for signature based monitoring in areas of the networks that probe based solutions are blind.



