In part three of this series we discussed how the Parisian authorities were unable to properly respond to their suspicions about “The Shoe Bomber” because they didn’t have adequate information. Another issue they had was they didn’t know how to respond to their suspicions. They knew to interrogate Reid but when that didn’t yield a confession, they were at a loss. In any security evolution, having appropriate procedures are often the difference between success and failure.
Blessed Flowcharts
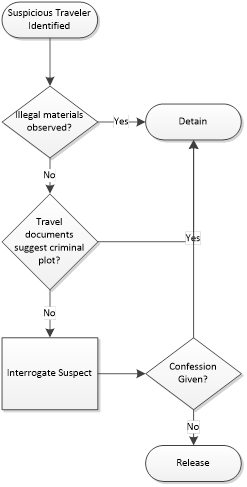
I am known as something of a flowchart nut. I spent years using them when I fixed jet aircraft and later created them to instruct on incident response and business processes. The reasons most people find flowcharts to be a waste of time is because they appear to contain “common sense” steps. Below, to the left, I’ve created a flowchart that represents the process used the day before the attempted shoe bombing.
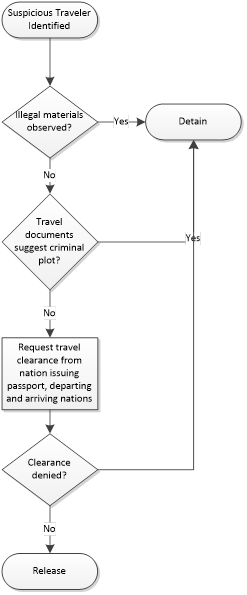
As you examine the flowchart it becomes pretty clear that it is far from “air tight.” It was unlikely to win approval by supervising security managers if put under the scrutiny of review. This is a good example of how flowcharts can show that processes are lacking full coverage. I’ve taken a stab at a “better” flowchart on the right designed to foil Reid’s exploit type.
December 21, 2001 Workflow |
Better Workflow |
|
|
|
Processes in Pencil
Once a process in place, it is time for the “devil’s advocates” in the organization to begin asking the “what do we do if…?” questions. As we learned in the last installment, the most insidious attackers have time on their side to gather reconnaissance on your processes and infrastructure and to make adjustments. This means that a key to winning the battle for your network is gathering intelligence on possible attacks and adjusting your processes to handle them.
Wildcards are Dangerous
One reason Reid slipped through the cracks was a more defined process wasn’t in place for his situation. If he was carrying a box cutter, hand gun or a passport with Pakistani entry stamps, the airport agents had a procedure to handle him. Since he didn’t fit into one of those molds the investigators made the human (albeit dangerous) conclusion of lowering the perceived threat. When dealing with wildcard threats on the network, they must be given the highest priority until the threat can be fully categorized. In network security, few philosophies can cause more harm than “it must just be an anomaly.” Assume it is deadly and have a process to handle all “unknown activity” until the mystery is resolved.
Protect Against Off Days (and Laziness)
The Shoe Bomber (and later the Underwear Bomber) launched his attack right before Christmas. It is a great time to attack because the travel infrastructure is most stretched and people are distracted by “visions of sugar plums.” The best criminals know to attack when the guard is down. Even the best of network security analysts have a bad day and the system needs to understand that. Logging and reporting of security process events are critical pieces of keeping bombs from going off. A flowchart on the wall doesn’t enforce the execution of the processes it represents. There needs to be audit trails, sharing with other concerned parties and a quality assurance (compliance enforcement) process in place. Failing to have policy review will allow the best analysts to become lazy and make the best intelligence gathering infrastructure impotent. If an operator can hit the “snooze button” on a potential shoe bomb, devastating results can occur.
Wrap Up
In this series we took a look at how the lessons from handling airport terrorist activities can ground us in modern network security. Every organization needs to be able to identify the worst types of advanced persistent threats by intelligently analyzing all available network data. Sound incident response procedures and workflow review need to be tied to these efforts to prevent disaster. We live in a dangerous world but some sound approaches to information security can keep the shoe bombers off our networks.