User-Centric Investigations
Investigating Organic Assets
Traditionally, network security tools focused on the malicious behavior of the endpoints. In recent months, it has become increasingly important to look at the human operators behind those computers. Investigations are increasingly beginning as a result of human intelligence in regards to user intentions or behavior. Disgruntled employees and “moles” pose a real threat to the safety of an organization. Reports of criminal activity from law enforcement or other employees need to be taken seriously, and investigators require the right tools in order to follow up on these leads.
Mapping User Details to Flows
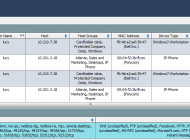
Lancope has long been a pioneer in accurately collecting and storing network metadata for forensic purposes. The recent release of StealthWatch 6.4 expands on that functionality by bringing user credentials down to the StealthWatch Flow Objects. Below is an enhanced StealthWatch Flow Object from the “Beron’s Folly” story I wrote about in an earlier blog entry, showing the availability of the user name and MAC address on the StealthWatch Flow Object.
Gathering the Identity Data
StealthWatch 6.4 is able to gather identity data from Cisco’s Identity Services Engine (ISE), StealthWatch IDentity™ appliance and from NetFlow export on Cisco ASA firewalls.
New Workflow
With the data existing in the StealthWatch Flow Object, user-centric workflows are now available.
Lucy Has Some Explaining to Do
Let’s examine a scenario in which Human Resources has been informed by an employee that user ‘Lucy’ is suspected of selling cardholder data to a Warez site. The newest release of StealthWatch allows investigators to pull up a “User Snapshot” to view Lucy’s activity.
The ‘Identification’ tab of the User Snapshot provides the following pieces of information to investigators:
- Machines Lucy authenticated onto the network
- Physical location of the machines by switch and switch port
- Device type of each host
- Date stamps on session authentication
- Services and applications utilized across each machine

The “Most Recent Flows” tab shows communications that Lucy currently has open.

The “Alarms” tab shows all security or performance events that have been mapped to Lucy.

One of the listed alarms is a “Suspect Data Loss” originating from a machine containing cardholder data. Running a flow table against that alarm reveals the following StealthWatch Flow Object.

The StealthWatch Flow Object shows that Lucy initiated a 2.33 GB upload to an FTP server in China from a machine containing cardholder data. With only a few clicks, investigators are able to use the cataloged information to verify the suspicions brought to HR.
User Identifiers of Compromise
In an earlier blog entry, we examined how identifiers of compromise (IOC) can be applied to StealthWatch Flow Objects to look retroactively for compromise. In StealthWatch 6.4, the user element has been added as an additional data point. This allows for historical analysis of behavior associated with a specific user, such as unauthorized access.
Wrap Up
In modern environments, being able to start investigations at the user level is increasingly important. StealthWatch 6.4 provides investigators with the data and dashboards needed to scrutinize user behavior both historically and in near real time.
Click here for more information on user-centric investigations and other new capabilities in StealthWatch 6.4.


