Cozumel Night Dive - Octopus
A great shot of an octopus on a night dive on my last trup to Cozumel.
Mindfulness "Mood Scene"
Mental Health "Break"
Artificial Narrow Intelligence (ANI) in Cybersecurity
BSidesSPFD - SECOPS Driving Prosecution via a Global CyberGrid
In a 2021 DarkReading article titled Handcuffs over AI, I describe the importance focusing on the outcome of increasing deterence in cybercrime. The presentation can be downloaded here.
2025 Conference Talks for Charles Herring
The following abstracts are available for delivery at security meetings and conferences.
Charles’ Biography
Charles Herring is co-Founder and Chief Technology Officer at WitFoo. WitFoo was founded to enable the sharing of information and operations across the craft of Cybersecurity. Charles leads research and development of the WitFoo Precinct platform that utilizes Apache Cassandra as a fundamental component in its architecture. Precinct ingests trillions of messages each day across hundreds of clusters to detect cybercrime and provide secure methods of sharing data and operations across corporations, organizations, law enforcement, national security and insurers.
Profit and Loss (PNL) of Cyber Security
The purpose of a CISO and a cyber program is to reduce the costs associated with cybersecurity. I said this to colleagues at a social mixer this week and their heads almost exploded. “Shouldn’t we be trying to stop and mitigate risk?” “We need to spend more money on cyber, not less.” “I can’t believe you, of all people, think we need to be doing less!”
Audacious Proposal
“Do you want to give up and let the bad guys win?” I want businesses to understand that cybercrime is a part of business in the exact same (not metaphorical) way as shoplifting, employees stealing office supplies, customers slipping on the floor, vandalism, executives abusing power against employees, hurricanes, power failures, earthquakes, flooding and taxes.
The goal in all risk management is to reduce the costs associated with the mishaps not to make them impossible.
Log4J/LogShell IOC search
Log4J/LogShell (CVE-2021-44228) exploit IOC have been published by Cisco Talos (see: https://blog.talosintelligence.com/2021/12/apache-log4j-rce-vulnerability.html). These IOC have been packaged as a WitFoo Actor definition and have been pushed to all production instances of WitFoo Precinct and Precinct Cloud. The definitions were automatically applied at 1404 Eastern Standard time on December 14, 2021. Detections are both forward looking and retrospective across the entire Precinct big-data archive.
Actor functionality has been pushed early (ahead of 6.2 GA release) to allow data to be searched. A quick overview of the functionality can be viewed below.
Emergency Update for CVE-2021-44228 (log4j / Log4Shell)
CVE-2021-44228 (https://nvd.nist.gov/vuln/detail/CVE-2021-44228) was released on December 10, 2021 outlining a vulnerability in Apache Foundation project Log4j (https://logging.apache.org/log4j/2.x/index.html). This vulnerability can be used by a remote attacker to execute code without authentication. This vulnerability is also known as Log4Shell.
WitFoo Precinct 6.x utilizes log4j in the WitFoo Streamer & Apache Kafka Docker containers that manage the message processing pipeline. Other custom WitFoo containers (including Cassandra 4.01) do not utilize log4j.
As of 0940 Eastern Standard time on Saturday, December 11, 2021, WitFoo has completed the following mitigation steps:
Lava & Cyber Insurance
I have been fortunate enough to have the opportunity to spend October on the Big Island of Hawai’i at a friend’s home while we button up the 6.2 release of Precinct. My wife and I were able to visit the Crater Overlook at Mount Kīlauea this week. Mount Kīlauea is the home of the Hawai’ian goddess Pele who controls the flow of lava (among other things.) Peering over the crater to see new earth being born under a canopy of ancient stars was breath taking and quite frankly an existential experience.
No Such Thing as Lava Insurance
In talking to locals, we were surprised to learn how inexpensive real estate is on the Big Island. When we inquired why that was true, we learned that there is no such thing as lava insurance. Driving the 2 hours from Waimea to the peak of Mount Kīlauea, we observed large lava flows dotted with huts and temporary housing that have accepted that another destructive lava flow is imminent.
GrrCon 2021: Machine Learning Driven Social Engineering
Machine Learning Driven Social Engineering talk will be given at GrrCon on 9/16/2021 at 4:30pm.
Abstract
Machine learning (ML) is arguably the most potent advancement in technology since atomic fission with similar benefit and risk extremes. The outcome driven nature of machine learning allows computers to rapidly test theories to find pathways to support specific goals. These approaches applied to social engineering can be used to manipulate human factors for purposes including cybersecurity breach. This session will cover the philosophies, strategies and tactics used to accomplish a successful campaign to recruit human assets to a cause. Factors to mitigate risk in these advanced social engineering attacks will also be examined.
2020 FBI Internet Crime Report
The 2020 Internet Crime Report from the FBI’s Internet Crime Complaint Center (IC3) has been released and can be viewed here: 2020_IC3Report.pdf. I highly recommend all in SECOPS take a moment to grok the content. I’d like to share a few of my observations.
High Level Takeaways
Reading the report reinforces a few concepts that have not yet made it into the mainstream thought of SECOPS:
Eventual Consistency in Business Meetings
Brewers CAP Theorem
Computer Scientist, Eric Brewer, stipulated in the theorem that carries his name that you can have two out of three guarantees in distributed data storage with the guarantees being consistency, availability and partition tolerance. The limitations in Brewer’s “CAP” Theorem are not only key in solving modern big-data challenges, they also are critical in solving big-business issues.
Business as a Data Lake
It may be that 6 years running hundreds of experiments across different data philosophies and platforms have created long-term trauma that makes every problem in life look like a big-data problem but I cannot help but notice some parallel lessons between data lakes and organizations.
WitFooPi – Precinct on a Raspberry Pi 4
Raspberry Pi is a fantastic tool for learning and experimentation. To assist our trainers, students and partners, we have created a build of Precinct to run on a Raspberry PI4. The WitFooPi is not supported as a production appliance but is great way to have Precinct in the palm of your hand for capture the flag, session training and lab testing.
Build Requirements
WitFooPi has the following requirements. Precinct performs advanced analysis on data and will stretch the ARM architecture to its limits. Active cooling is a must to prevent overheating the unit. You will also need a 128GB SD Card, a Pi enabled Precinct license and the Pi image file.
Cassandra 4.0 Testing
WitFoo Precinct persists and replicates data on big-data NoSQL platform Apache Cassandra. Precinct 6.1.3 is built on Cassandra 3.11. In preparation for upgrade to Cassandra 4.0, the following lab & production testing was conducted.
Lab Appliances
WitFoo Precinct clusters consisting of 1 Management, 1 Streamer and 3 Data nodes were deployed in AWS using the official Marketplace images. The instances were configured to use AWS GP2 SSD drives (the recommended default) and were running on c5d.2xlarge hardware (16GB RAM, 8 CPU Cores.)
Our Move from Elastic to Cassandra
When we founded WitFoo five years ago, we wanted to analyze data in SIEM and other data stacks to provide craft knowledge that would stabilize communications within cybersecurity teams and between those teams and their organizations. A few months into that journey we realized there were fundamental problems in how existing SIEM and log aggregators collected and stored data which prompted us to add big data processing to the scope of our venture.
Fake Cybersecurity Awards
Cybersecurity expert, Chris Roberts, lamented earlier today in a LinkedIn post that he was offered a cybersecurity award for the low price of $1,200. His outrage prompted me to realize that most cybersecurity professionals and decision makers do not get the opportunity to see the evidence many of the “awards” in cybersecurity are bogus. I took a few minutes to search my email archives for some of the pay to play awards we have received in recent months.
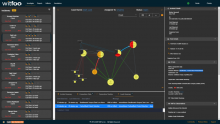
Searching Precinct for Solarwinds Breach
Searching for the TLD of the Solarwinds DGA will quickly reveal any hits reported to Precinct. The TLD to search is avsmcloud.com. Months of incident data can be searched in moments and full, big-data search can run as a job.
Note, there have been no reports of matches from WitFoo customers at this time. IOC’s associated with the breach have not been submitted to WitFoo Library.
If you require assistance in running these searches, please reach out to WitFoo Support.
18 Years of Getting SOAR to Fly
On Emergency Leave on 9/11
In September of 2001, I had been on active duty in the US Navy for 6 years. I was stationed with the World-Famous Golden Dragons of VFA-192 in Atsugi, Japan, running the night shift of the Integrated Weapons Team. On the morning of September 11th, 2001, I was in South Carolina on emergency leave from my squadron-mates because my mother was in intensive care. It was already a traumatic time in my life before the news of the Twin Towers woke me from my sleep. A few minutes later, my division officer called to see how much time I needed before getting on the first plane back to Japan. I fully expected to join my squadron on another tour of the Persian Gulf on the USS Kitty Hawk and extend my tour overseas. I had no idea how much my life was about to change and how different it would be from what I had planned.
2021 Conference Talks from Charles Herring
Bio
CHARLES HERRING
WitFoo Chief Technology Officer
Triangulating a Sustainable Revolution
By the end of 2015 it was clear to me that the craft of cybersecurity was broken. My mind continuously compared SECOPS with other mature crafts that I had observed and executed, and it bothered me to the point of stealing peace and sleep. I decided I was going to start a revolution to “Build the tools and data needed to enable the craft of cybersecurity operations to mature.” This focus formed the mission of WitFoo and the battle cry for the revolution. Most revolutions fail because there is a myriad of devious factors stacked against them. Most Davids are murdered by Goliath. It is very rare for bold, underdog revolutions to succeed. We knew that even before we filed Articles of Incorporation. We knew to deliver sustainable, healthy change into a toxic market, we were going to have to have a set of plans resilient to the dangers and evils that existed.
The Rock & Roll of Startup Development
Rock On
For the last 4-5 years of running with the WitFoo revolution, I have constantly had to defend our small team. In the early days, potential investors would remark, “You can’t get all this done with such a small team.” Now that we have accomplished building the product, the go-to-market strategy, have many happy customers we are still told, “I don’t see how you can get so much done with such a small team.” I want to respond with “that seems to be a problem with your ability to see since we’ve already done it and you are looking at it,” but I realize that is not going to help the situation.
In dealing with customers, analysts, partners and investors I am regularly faced with having to decide whether I should acquiesce and deliver what they want or try to teach them why they should change their minds and accept what I believe they need.
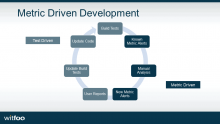
ExploitCON West 2020 Slides – Metric Driven SECDEVOPS
Slides of our talk can be downloaded here.
Details on the session are available here: https://exploitcon.com/#/west
WitFoo Global Community Indicator of Compromise (IOC) Feed Demo
WitFoo’s Global Indicator of Compromise feed is a secure and reliable way for the WitFoo community to share intelligence about emerging threat sources.
The feed is updated in near-real time as attacks occur across the WitFoo Community. It consists of the IP address and hostname of the attacking source, the tools and methods that the community is using to detect the threat and how many incidents the source has been a part of across the community.
Hits in the feed are automatically shared across the entire community and big data stacks of each deployment are retrospectively analyzed to find hits that may have been missed. All records including firewall, proxy, EDR and NetFlow records are checked for communications with the known bad indicators.