The Challenges of Trust
Traitors have been making history throughout the ages. Some traitors are regarded as revolutionaries. Some are infamously despised. Regardless of how history regards an individual that betrays his current allegiance, it is categorically devastating for the betrayed organization.
Constructive and Destructive Power of Trust
The reason that debilitating betrayal is possible is because trust is empowering to the bestowing organization. All business founders soon discover that they must delegate areas of responsibility to others. To enable these delegates to effectively accomplish their responsibilities, they must be given privileged information, access and power. This creates opportunities for the misappropriation of the office the trusted employee fills. The more trust an individual is given, the more risk they pose to an organization.
Mitigating Risk of Betrayal
There have been many different approaches over the centuries to reduce the risk of an insider executing betrayal on their patrons. The first risk reduction approach is reducing access and power to the minimal level required to perform functions. This approach tends to restrict innovation and slow progress but is nonetheless effective in reducing the destructive effects of betrayal.
Screening
Because risk must be accepted for effective delegation to occur, enforcement tends to not be the best method for preventing betrayal. Military organizations have long used a security clearance model of examining the trustworthiness of a given officer. Many corporate organizations have also adopted this model of reviewing the potential of betrayal in this manner.
Monitoring
In addition to initial and ongoing screenings, watching the actions of trusted delegates is critical. The more trust, access and power given to an individual, the more monitoring required. Servicemen with low level security clearances are monitored much less than those that have access to nuclear weapons. The same must be true in information security and throughout an organization.
Betrayal in InfoSec
Information and network security runs into the same problems that physical and martial security have.
I Finally Say Snowden
In recent months, the insider threats of Edward Snowden and Bradley Manning have made the headlines. They are popular topics for a number of political, social and technological reasons as well as for the intrigue they bring. They are great case studies in information security because they reveal that even secured facilities within the U.S. DoD are extremely vulnerable when a trusted administrator finds reason to betray the trust of his benefactors.
Motivations for Betrayal
The motivations that turn insiders against their organizations are diverse.
Activism
In the case of Snowden and Manning, the apparent motivations are what we normally call activism. Activists are associated with a particular ideological movement. Activism makes it into the news cycle much more regularly than other motivations for betrayal because it is the nature of activists to drive a dialog. This requires the advertisement of their activities. As a result, a much higher percentage of ideologically motivated breaches become well documented.
Greed
There is probably no better motivation for crime than greed. Bribing an underpaid administrator to deliver access to an attacker is an extremely effective breach method. Social networks like LinkedIn make it easy for attackers to determine who they should wave money at. In addition to being an effective way of gaining access to a network, privileged users normally have the ability to make detailed plans that allow them to stay undetected in the network for years. They can provide attackers with email addresses to target for spear phishing so when investigators start looking at logs it looks like stolen credentials were gained that way (instead of resetting passwords or cracking stored hashes).
Disgruntled Employees
It is the nature of an employee to have some degree of displeasure with his employer. When the displeasure grows to dangerous levels, the employee may attempt to harm his organization through whatever means available.
Extortion
One of the most effective ways of turning the loyalty of a privileged user is extortion. The discovery (or manufacturing) of marital infidelity or crimes can be used as leverage to force an otherwise loyal employee into a compromising position. In extreme cases, kidnapping or threats of violence can also be used.
Espionage
“Planting” a resource in a victim’s organization who feigns loyalty for the sake of betraying the victim for the attacker’s gain is espionage. Nations have been doing this for as long as there have been nations. In recent years, corporate “plants” have been used to extract information from the inside.
Catching Insider Threats
When insiders become a threat to the organization, how can they be detected and contained? It is a complicated answer that includes human intelligence in the workplace, regular background checks and closely monitoring behavior on the network.
Catching Insider Threats with the StealthWatch System
Thanks to the deep, pervasive network visibility that the Lancope StealthWatch System constructs through the use of NetFlow, the network behavior of every user on the network can be monitored. As mentioned earlier, the higher the level of trust, the more closely the individual needs to be observed.
Unauthorized Access
When a user attempts to access resources on the network that are prohibited, security events are fired in the StealthWatch System. In the screenshot below, notice that user “Vernon” is attempting to make connections prohibited by enforcement mechanisms. This could be an early indication of a breach to come. It should lead to questioning of Vernon’s behavior and assessment of his risk to the organization.

Policy Violations
When users begin using services that are in direct violation of company policy and are intended to bypass company monitoring, immediate red flags should trigger. In the communications below, a user is noted as using a tunneling technology to hide the nature of Internet communications.

Internal Reconnaissance
Before insider threats can extract data, they must first inventory it. The following illustrates internal scanning looking for file shares to evaluate for theft.

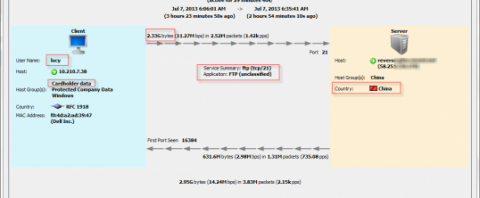
Suspect Data Loss
When compromised, privileged users send abnormal amounts of information out of the network, alarms should trigger. In the example below, Lucy discloses several gigabytes of traffic from a server containing sensitive data to an FTP server in China.


Suspect Data Hoarding
In cases where administrators download large amounts of information to either upload out of the network or download to removable media, evaluating the total bytes they are collecting/hoarding is necessary. Utilizing the Host Snapshots contained in the StealthWatch System, collective data hoarding over time can be alarmed against an endpoint. In the example below, user “Danielle” has collected 1.7GB of data to her machine (which exceeds baseline acceptable levels). The benefit of the Suspect Data Hoarding alarm in the StealthWatch System is that it allows downloads over time from diverse data sources to alarm when other detection methods would fail to trigger.

Target Data Hoarding
Target Data Hoarding focuses on data being extracted from a given source. When abnormal transfers from a host containing sensitive data occur (even from dispersed clients), an alarm will trigger in the StealthWatch System. This is particularly helpful in catching insider threats that have access to multiple endpoints on the network they can use for hoarding. This type of data collection may delay detection via Suspect Data Hoarding if a sufficient number of data collectors are used, but will be revealed in Target Data Hoarding since the focus is on the collective amount of data leaving protected network assets irrespective of the client.
Audit Trails
In addition to the monitoring and detection mechanisms listed above, forensically logging every communication a user makes on the network can be extremely useful when concerns are raised outside of automated monitoring. When managers or co-workers note abnormal behavior or attitudes, the network behavior can be retroactively analyzed to look for further evidence of risk.
Wrap Up
Insider threats are one of the hardest attack vectors to thwart. Hiring practices, employee management, human intelligence and proper security controls all play an important role in preventing these types of breaches from occurring. In addition to these areas, pervasive logging and monitoring of all network activities in which privileged users participate is of paramount importance. The advanced threat detection and forensic logging of the StealthWatch System can make it much harder for a trusted resource to become a turncoat.
