Spear Phish Detection and Response
Charles Herring
20 September 2013
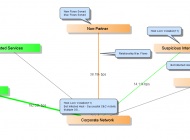
The difficulty in controlling user behavior makes spear phishing a "no-brainer" for attackers. Network surviellance can detect the attack at different parts of the kill chain.