Can’t Patch a User
Every security professional and IT administrator knows the importance of keeping computing assets patched against known vulnerabilities. “Scheduled maintenance outages” and “Patch Tuesdays” are staple phrases to even end-users. A major challenge in protecting computer networks and the data on them is that user behavior is difficult to “patch.” The 2013 Verizon Data Breach Investigations Report (DBIR) found that 76% of breaches occurred via exploitation of “weak or stolen credentials.” This shows that the easiest way for attackers to get into the network is to trick users into disclosing their credentials.
Anatomy of Spear Phishing
One of the most popular (and effective) ways to steal credentials is through spear phishing. An attacker will craft a convincing prompt to solicit credentials. A good message will look much like a valid communication from official company administrators.

If a user trusts the email, they will land on a website that looks legitimate prompting for credentials. “Patched”/trained users may notice the suspicious elements of the website and email but less savvy users will not. Also, skilled attackers will go through the trouble of using a better domain name than I’m using here (like lanccope.com) and even purchase a trusted certificate to remove certificate errors even further reducing suspicion.

Filling out the above form will not actually change the user’s password but will give the current one to attackers.
Detecting Spear Phishing
There are email scanning solutions on the market that look for tell-tale signs of spear phishing as demonstrated above. These solutions have varying degrees of effectiveness but as discussed in “When Enforcement Doesn’t…”, failure to monitor network traffic will give attackers enough time to craft an attack that will bypass these filtering solutions. Intelligent network monitoring with Lancope's StealthWatch can alert operators to the different stages of even the most advanced spear phishing attacks.
Reconnaissance
For an attacker to be most successful in extracting user credentials, he has to do his homework. At least two things have to be established. First, the attacker needs to fingerprint the mail servers that will be processing the dangerous email. The discovery and fingerprinting of email servers can be quickly detected and mitigated against using StealthWatch.

Once the email servers have been evaluated and a method for bypassing scanners has been crafted, a compelling web page needs to be created. The same reconnaissance will occur. The style of one of the valid websites will be cloned on the phishing website.
Delivery of Mail
Once the email is crafted it has to be delivered to user targets. StealthWatch tracks and baseline the behavior of mail generation both coming into the network and leaving it. When the attacker delivers messages, the anomalous volume of email triggers alarms.

Clicking the Link
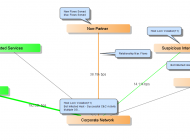
As users receive the email and click the link, StealthWatch will monitor for any anomalous traffic profiles by geography and trust. Below is a relationship map showing an abnormal number of connections originating from the corporate network going to servers geographically located in Asia.
This type of detection would have been helpful in the South Carolina Department of Revenue breach that occurred earlier in the year. Spear phishing was used by a Russian based attacker. SC DOR has rare occasion to communicate with Russia and would have triggered alarms at this point in the Kill Chain.

In addition to monitoring for geographic based anomalies, StealthWatch also monitors for anomalous traffic based on corporate trust of external hosts. In the graphic below, the spear phish web application falls into “Non-partner” trust and has triggered alarms both at the host and relationship levels because of the unexpected pattern of traffic.
Credential Use
Using the same methods described above when the attackers use the stolen credentials, alarms will also trigger because of their anomalous nature. Additionally, as credentials are used in geographically improbably scenarios, StealthWatch will render this information to investigators (also see: “User-Centric Investigations.”)

Internal Pivot and Data Theft
Once an attacker has circumvented the perimeter defenses, lateral/pervasive monitoring becomes essential. NetFlow and behavioral analysis becomes a critical component in detecting internal pivots and data theft/staging. In the entry, “Looking East and West”, details on monitoring a compromised asset via intelligent NetFlow analysis are explained.
Post Attack Analysis
Once a spear phish attack is detected and cleaned up there are a few important steps necessary to improve readiness for the next round of attacks. The first is to determine impact. The following questions can be easily answered via NetFlow.
- Which users and machines were compromised? (see: Has APT1 Been Eating My Porridge?)
- What data did the compromised machines access? (see: Looking East and West)
- Did protected data leave the network? (see: Monitoring Protected Data with NetFlow)
Once impact is determined, the collected data can be used to improve and audit enforcement mechanisms (see: When Enforcement Doesn’t…).
Wrap Up
Spear phishing is an effective attack vector used by attackers to steal user data. The challenge of training all corporate personnel to detect this type of attack is not currently possible. Enforcement mechanisms that are designed to thwart phishing are bypassed due to poor security intelligence. Intelligent behavioral analysis of NetFlow with Lancope's StealthWatch can provide visibility into each step of these types of attacks, validate enforcement efficiency and provide critical data for incident response.

