Processing IOCs in the StealthWatch System
Charles Herring
13 March 2014
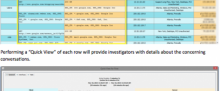
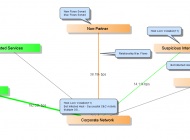
Threat data contained in Indicators of Compromise (IOC) can be applied against the data stored in StealthWatch to look for markers of historical breach. This entry outlines the steps in performing this analysis.